Many companies have rapidly adopted home working. With the spread of remote working, it has never been more important for IT administrators to ensure that all their company's devices are secure, even if they don't belong to the company.
Google has pioneered zero-trust security as part of its BeyondCorp strategy. And this provides advanced security for Google Workspace users to ensure secure access to all devices. Administrators can apply these controls to Google Workspace applications and to third-party enterprise applications and data, ensuring consistent security and user experience across your organization.
Secure mobile and desktop devices with endpoint management


BYOD devices can vary considerably from company to company, with a range of operating system versions, hardware modes, patch versions and so on. With Google Device Management, IT administrators can easily support this variety of devices by enforcing measures such as minimum software versions and blocking jailbroken or rooted devices, in many cases without requiring full device rights to preserve employee privacy.
When it comes to mobile device management, Google Workspace offers basic and advanced mobile device management:
- With basic mobile device management, BYOD devices are secured with basic security functions, without the end user having to worry about a thing. Administrators can impose a passcode, obtain a device inventory, remotely delete Google accounts and even remotely install applications on Android devices.
- With advanced mobile device management, administrators can apply more controls over BYOD devices, and Android users can keep their personal data private and separate from their business data with Android work profiles. You can also authorize and manage business applications on iOS and Android devices.


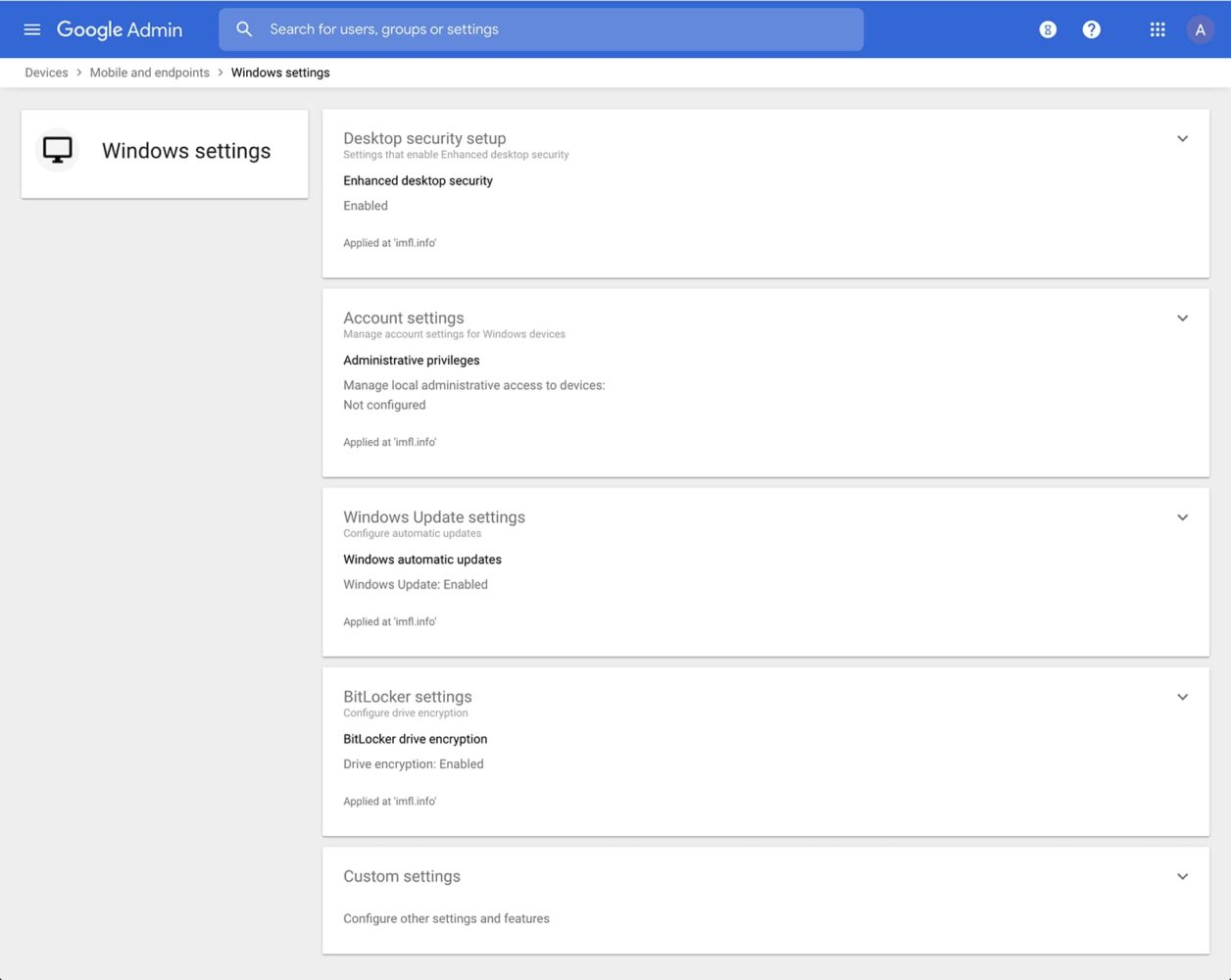

Administrators can also manage and secure computers with basic device management and enhanced security for Windows. With basic device management, when a user connects to Workspace via any browser on a Windows, Mac, Chrome or Linux device, that device is automatically enrolled in endpoint management. This ensures a basic level of security for every desktop device accessing data on Workspace. With Advanced Security for Windows, administrators can easily manage and secure Windows 10 devices via the administration console.
Enable secure VPN-free connections with context-sensitive access rules


Contextual access offers protection against unwanted access to Google Workspace services without the need for a VPN. These features enable administrators to define different levels of access based on the user's identity and the context of the request, taking into account factors such as country, device security status and the request's IP address. For example, you can require BYOD devices accessing Workspace to meet encryption and password requirements, or prohibit subcontractors from accessing Workspace from company-managed Chromebooks.
Control data access with application access control
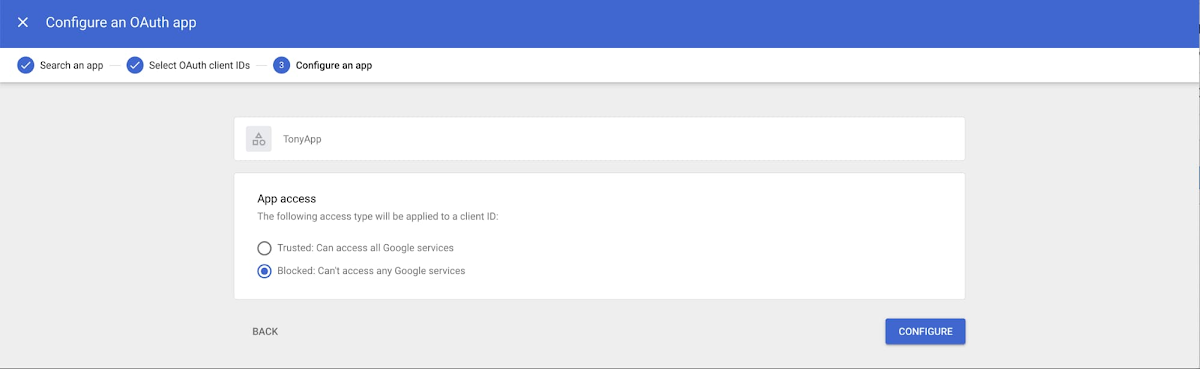

It's important to protect all your company's devices, whether corporate or BYOD, from malicious applications attempting to access corporate data. With application access control, administrators can take steps to prevent these applications from misleading users and mistakenly granting them access to company data. With this feature, administrators can choose which third-party applications are allowed to access users' Google Workspace data by explicitly allowing, restricting or blocking application access.
Activate two-step verification


With two-step authentication, administrators can reduce the risk of unauthorized access by asking users for additional proof of identity when logging in. And you can now use the Advanced Protection Program, our strongest protection for users at risk from targeted attacks. With Advanced Protection for Business, we'll apply a specific set of rules for registered users, including enforcement of security keys, blocking access to untrusted applications and enhanced e-mail threat analysis.
If you choose not to use security keys for any reason, you have several other options for applying two-step verification on BYOD devices. For Android and iOS, you can use the Google prompt, Google Authenticator, text message or phone call options for a second verification step.
Last but not least, you can now activate password-free log-in via access keys. For example, a user's biometric fingerprint is enough to authenticate him or her. They no longer need to enter a password and a second factor to log in.
Prevent data loss and leakage with DLP (data loss prevention) functions


Data Loss Prevention (DLP) policies help you protect sensitive information in Drive, Docs, Sheets, Slides and Gmail from loss, misuse or access by unauthorized users. Administrators can choose which types of data are sensitive and how to protect them. Controls easily detect a wide variety of common information types, and administrators can supplement these with customized content detectors to suit their organization's needs. You can also automatically classify files in Drive using DLP rules to categorize your data by sensitivity level. DLP works on all your organization's devices, including BYOD devices, since protection is at data and application level.
In addition to DLP, you can use DXP for iOS devices to restrict the copy/paste of Workspace data to other accounts, personal or otherwise. DXP for iOS can also restrict users' ability to drag and drop files from specific applications within their Workspace account. Similarly, you can use Google Device Management to configure Android devices to prevent data sharing between personal and professional profiles.
With Vault, preservation and eDiscovery are possible on all your devices
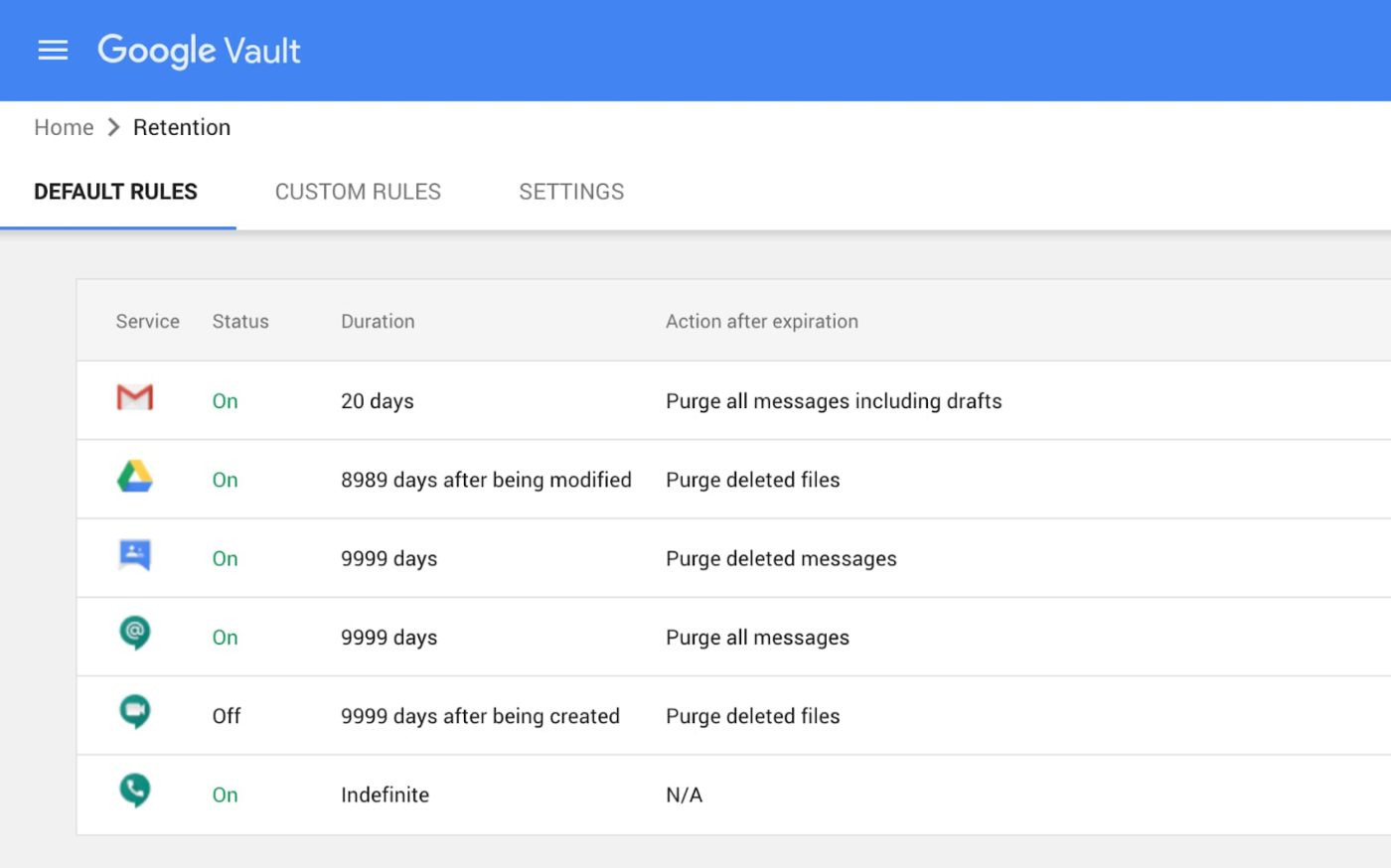

To meet your company's retention and eDiscovery needs, Vault makes corporate data stored in Google Workspace and accessible via BYOD devices available for all your information governance needs. No matter who owns the device, your corporate data stored in Gmail, Drive, Chat, Groups, Voice and Meet is accessible to Vault.
Using the zero-trust security model, the Google Workspace features above work together to protect your data and secure your organization on all devices, whether company-owned or BYOD.
Easy, intuitive management
Google Workspace features simple, intuitive management of all security settings. It takes just a few clicks to configure Google Chrome browsers company-wide, or set up a new security policy or customized alerts.
Illustrations by Google
Photo by Mikey Harris on Unsplash









Google Workspace superior to Microsoft 365
Hyperconnected: the brain at risk
Choosing a project management software